Comparing Inter-AS MPLS L3VPN Options (A, B, C)
When an L3VPN service needs to span across two different service providers, an Inter-AS L3VPN solution is required. This scenario is common for national or international circuits where a single service provider is not present in both locations. The routers connecting the two autonomous systems (AS) are known as Autonomous System Border Routers (ASBRs) or boundary routers. In this article I will go into the three primary options for connecting L3VPNs across autonomous system boundaries: Option A, Option B, and Option C, highlighting their distinct characteristics, operational mechanisms, and suitability for various deployment scenarios.
Inter-AS L3VPN Options: Overview
The following table summarizes the key differences between Inter-AS L3VPN Option A, Option B, and Option C, drawing from design considerations, scalability, security, and operational complexity
| Aspect |
Option A (Back-to-Back VRF) |
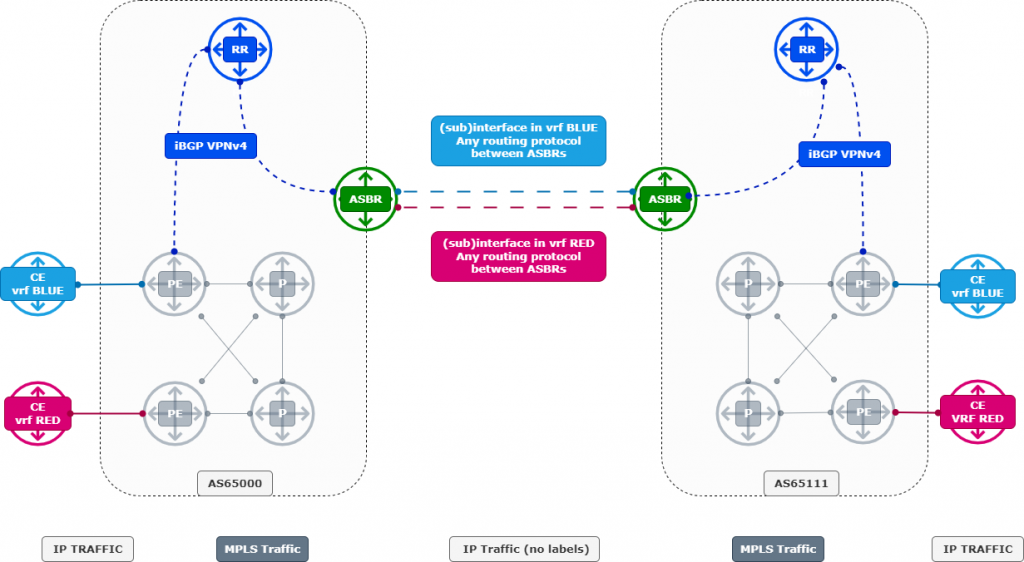
(VPNv4 between ASBRs) |
Option C (RR-to-RR VPNv4) |
|---|---|---|---|
| Scalability | Least scalable | Moderate | Highest |
| Security | Most secure | Lower | Lowest |
| Resource Utilization | High (per VRF state on ASBRs) | Moderate | Low (ASBRs only exchange loopbacks) |
| Label Handling | No MPLS between ASBRs | Yes, via BGP (RFC 3107) | Yes, via BGP LU + RT exchange |
| Complexity | Simple | More complex | Very complex |
| BGP AF | IPv4 per VRF | VPNv4 | VPNv4 (multihop) |
| Typical Use Case | Small deployments, high security | Medium scale, simpler than C | Large-scale carriers, scalability focus |